10 App Security Terms You Should Know
Welcome to Secumantra! We already learnt what is OWASP and OWASP Top Ten in our previous post. Before we look each one of these items in detail, we must build our vocabulary to have basic understanding of some of the commonly used security terms. To start with, we will focus on top ten such terms in this post.
For a security professional, it is important to understand these terms and relationships between them to handle security issues in a better way. Knowing these terms will help you to have fair idea about impacts of different security risks and you will be in a better position to prioritize the countermeasure.
It will also help understanding OWASP Top Ten risks in a better way and when you do threat modeling for your system. Threat modeling is a technique which helps to identify threats, vulnerabilities, and mitigation in the context of your web application. We will have a separate post on this topic soon.
1. Asset
An asset is a valuable resource which we want to protect. It can be a physical hardware, software applications or the sensitive data these applications handle. In order to protect these assets, we must understand the possible ways an external entity can enter inside our trust boundary.
The definition of asset varies by perspective. For an organization, an asset might be the availability of information, or the information itself, such as customer data. It might be intangible, such as your company’s reputation. To an attacker, an asset could be the ability to misuse your application for unauthorized access to data or privileged operations.
It is the fundamental aspect which decides overall security considerations for your applications. Security professionals will decide mitigation strategy depending on the value of these assets for a company i.e. criticality of the resources and data being handled.
2. Threat
A threat refers to an incident that has the potential to harm a system, company’s business or reputation. It can be unintentional (due to human errors by inside employees) or intentional (by hackers), but surely an undesired event. It could negatively affect an asset.
Worms and viruses are also categorized as threats because they could cause harm to your organization through exposure to an automated attack, as opposed to one perpetrated by humans.
These threats may be uncontrollable and often difficult or impossible to identify in advance. Still, certain measures help you assess threats regularly, so you can be better prepared when a situation does happen.
3. Vulnerability
A vulnerability is a weakness present in the system (we often refer it as an asset or resource) that makes an exploit possible. It is a known issue that can be exploited by an attacker to destroy, damage or compromise an asset.
As applications grow in size and complexity, you will have vulnerabilities present there. Let’s imagine these weaknesses as security bugs which can be used by hackers to access to sensitive information.
Vulnerabilities do not only occur in software systems, but can exist at physical level or at the network, and might be due to the flaws in operational processes. Testing for vulnerabilities is critical to ensuring the continued security of your systems. By identifying weak points, you can develop a strategy for quick response.
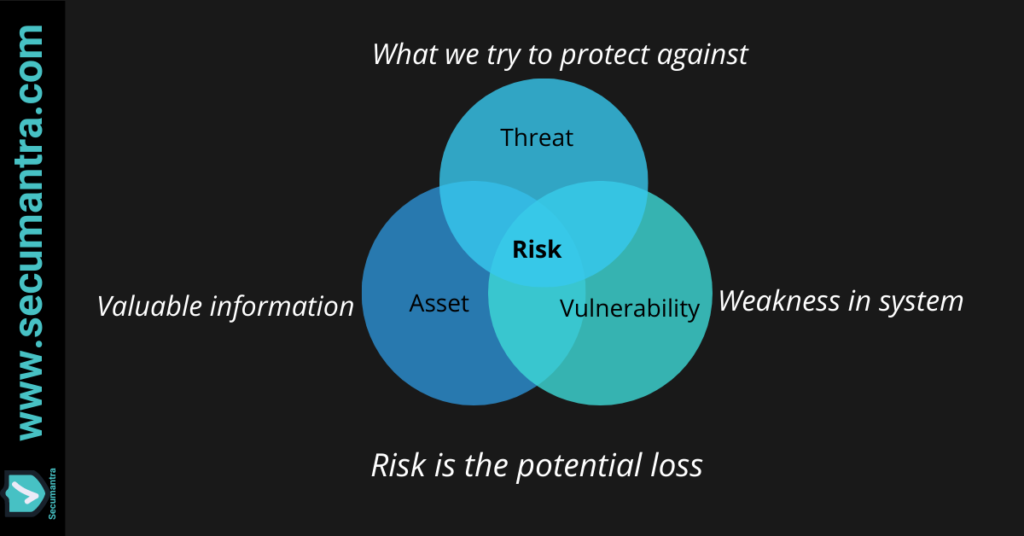
4. Risk
Now that we understand basic elements of information security we need to relate this with the possibility of loss that can occur if an asset is compromised due to the vulnerability present by a threat.
So in short, risk is a possibility of suffering a loss in the event of an attack. It is the potential loss or damage when a threat exploits a vulnerability. Examples of risk include financial losses, loss of privacy, reputational damage, legal implications, and even loss of life.
risk = threat probability * potential loss
Risk can also be defined as: Risk = Threat x Vulnerability
Identifying risks is very important as it helps to document, prioritize and secure your applications. It can be a tedious task and there exist some methodologies and tools to do risk assessment for the systems to be implemented.
It can happen that you identified a vulnerability, but there is no threat to exploit it, so you have little or no risk. Similarly, you might detect a threat but have already secured any weaknesses that it could exploit. So accurately assessing threats and identifying vulnerabilities is critical to understanding the risk to assets and prioritize accordingly.
5. Attack Vector
An attack vector is a path or method an attacker can gain unauthorized access to a network or computer system in order to execute a malicious payload. Attack vectors enable hackers to exploit system vulnerabilities, including the human element.
Hackers can steal user information or sensitive data from applications by exploring known attack vectors and attempting to exploit vulnerabilities to gain access to the targeted system.
Attack vectors include viruses, e-mail attachments, phishing, compromised credentials, misconfigurations or third party software. Some of these methods involve programming (or, in a few cases, hardware) in which a human operator is fooled into removing or weakening system defenses.
Securing potential attack vectors against exploitation by hackers requires IT organizations to implement policies and procedures that prevent hackers from obtaining useful information about IT security vulnerabilities.
6. Attack Surface
The total number of attack vectors an attacker can use to manipulate a network or computer system or extract data. A smaller attack surface can help make the organization less exploitable, reducing the risk.
It is very important to understand the difference between attack vector and attack surface. You need know the attack surface for your asset and try to reduce the attack vector points as much as possible.
7. Exploit (Attack)
An attack is an action taken that utilizes one or more vulnerabilities to realize a threat. This could be someone following through on a threat or exploiting a vulnerability.
It can be a piece of a software which will make use of the vulnerability in the system.
An exploit is a way to take advantage of a vulnerability in software. Typically, software updates patch these vulnerabilities, which is why it’s so important to update both your software and OS.
8. Data Breach
Data breach is a security incident where sensitive, protected, or confidential data is accessed or stolen by an unauthorized party. This confidential, or otherwise sensitive information then can be released publicly into an unsecured environment. A data breach can occur accidentally, or as the result of a deliberate attack.
Data breaches are a major concern for cyber-security because sensitive data is constantly being transmitted over the Internet. This continuous transfer of information makes it possible for attackers in any location to attempt data breaches on almost any user or business they choose.
It’s important to take steps to help protect your personal information and realize what happens when you share personal information. You likely have little control over how your information is secured or what could happen to it in the event of a data breach.
9. DoS Attack
A denial-of-service attack (DoS) is a type of attach vector. A DoS attack occurs when an attacker tries to make a service unreachable to legitimate users by flooding it with illegitimate requests. Often, this comes as a distributed denial-of-service attack (DDoS), where many different sources create the flood of traffic.
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. From a high level, a DDoS attack is like a traffic jam clogging up with highway, preventing regular traffic from arriving at its desired destination.
DDoS attacks can temporarily shut down websites, credit card payment services, and similar. When a server suddenly receives millions of requests per second, it simply can’t keep up with the traffic. This is similar to a large group of people cramming the door of a store so that normal customers can’t get in.
10. Countermeasure
Countermeasures address vulnerabilities to reduce the probability of attacks or the impacts of threats. They do not directly address threats; instead, they address the factors that define the threats. Sometimes they are referred as mitigations.
Countermeasures range from improving application design, or improving your code, to improving an operational practice.
Summary
As we mentioned at the start, we have just started here with top ten important terms and this is just a starting point. We will get to know more terms related to web application security as we visit each item from OWASP Top Ten list and other security topics in new posts.
Thank you for reading. Stay Safe, Stay Secure!