HTTPS – Everything You Need To Know!
Welcome to Secumantra! In this post, we will understand why HTTPS is needed and how exactly it works. We will also see some more benefits of securing your website with HTTPS.
Why HTTPS?
Many times we found HTTPS vocabulary little confusing and we tend to skip this topic. It eventually makes HTTPS a black box for us. Let’s understand different terms one by one and try to stitch them together.
HTTP
HTTP stands for HyperText Transfer Protocol. This is the most widely used web protocol in the world which is basically used to view web pages on internet. When we type web address like google.com in our browser tab, “http://” is automatically added at beginning. It indicates HTTP protocol being used for this website.
In standard HTTP protocol, all information is sent in clear text format. All communication and information exchange is transferred over the internet in simple text format and therefore vulnerable to hackers. For sensitive information like personal data, bank details etc. this is not what we expect and is a serious security problem. That’s why we need HTTPS!
Hacker who is interested in this information is sometimes referred as a man-in-the-middle. Sounds familiar?
Man in the Middle Attacks!
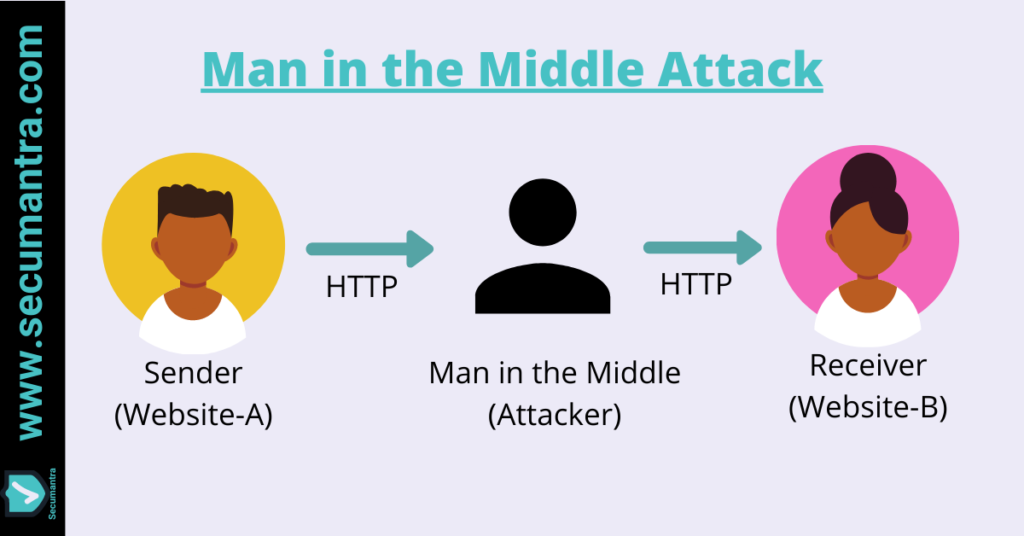
When two people are communicating, they don’t necessarily know that there exist a third person (man-in-the-middle). They only know they are communicating with each other.
When plain HTTP protocol is used, the content of the conversation is not protected in the transition. Now there are multiple points where man-in-the-middle can intercept the communication when we consider the typical working of the web. This is the real reason why we need HTTPS.
Imagine a browser running on a mobile device or desktop on one end. Now there is a communication channel between this device and the wireless router. We are sending all our communication through this device which can be controlled by an attacker. What if the attacker uses this router to redirect the traffic somewhere else?
For example, when a cafe or a public space offers a free WiFi which is not password protected as well. An attacker will gain full visibility to the communication, once a victim connects to such WiFi hotspot.
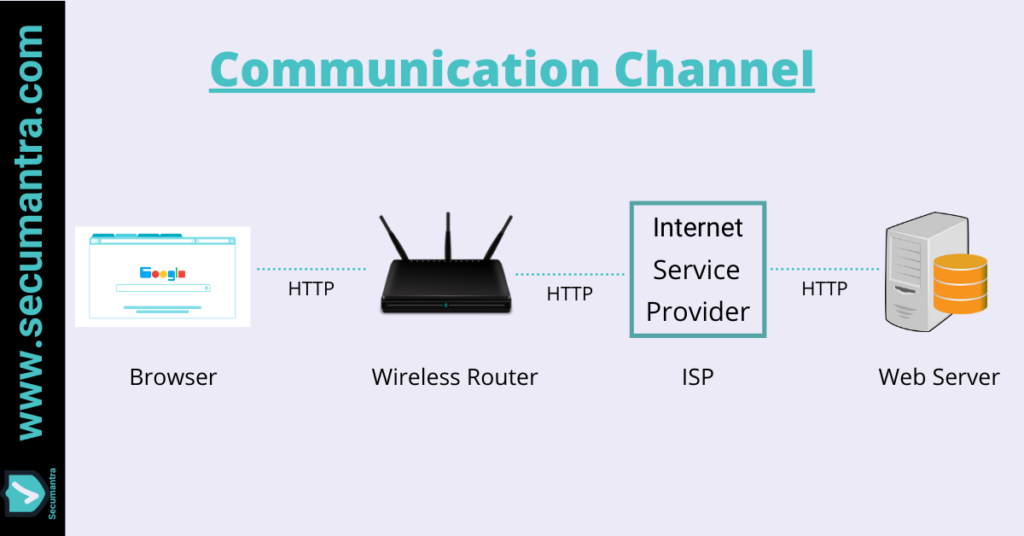
Note that this is not the end of communication and point of interception can happen at multiple such locations upstream. Wireless router has to go through ISP and ISP is connected to some web server. Everything between these different end points is possible location for man-in-the-middle attack.
How HTTPS Works?
HTTPS stands for Secure HyperText Transfer Protocol. It is the standard HTTP with additional layer of security. It uses different encryption algorithms to scramble the data that is being transferred over the internet.
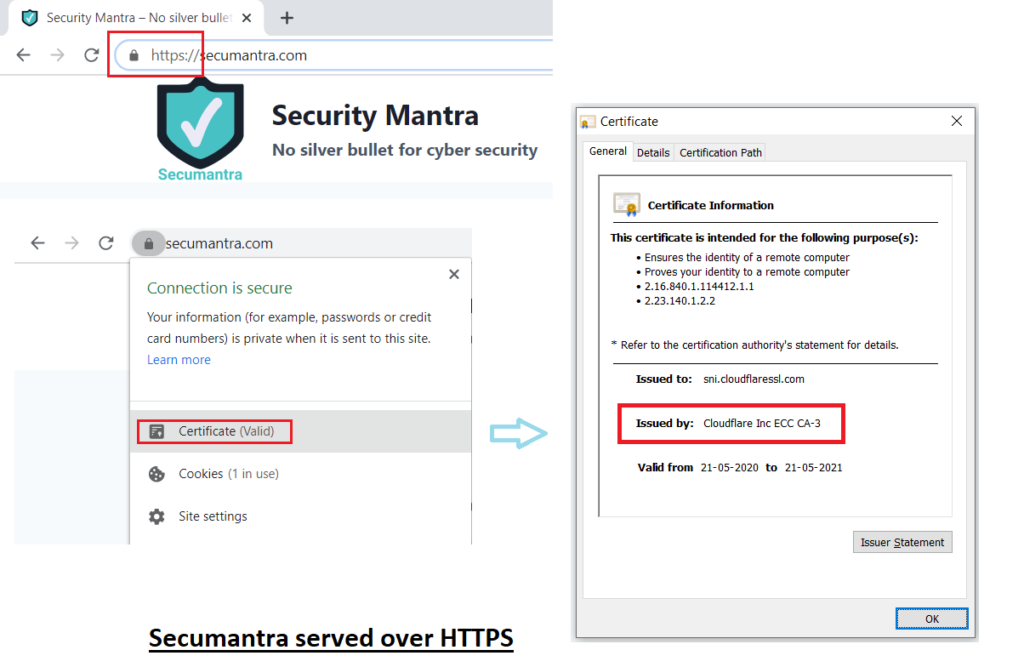
It is indicated by https:// and a padlock symbol in the URL. Just look at the current website URL in your browser and you can see https:// and the padlock. It shows SecuMantra is served over HTTPS and all communications are secured.
SSL and TLS
SSL (Secure Socket Layer) and TLS (Transport Layer Security) are the security protocols when we talk about HTTPS. SSL was originally built by Netscape back in early 1990s and has been used for many years.
TLS is successor to SSL and is widely used today. As there are two parties involved in communication, if server implements latest version but client can only work with TLS 1.0, then communication falls back to highest commonly supported protocol. With each new version we get faster and more secure communication, latest version being TLS 1.3.
SSL is not being used today as TLS has taken over it. Still people use these terms interchangeably and SSL is being used when we actually mean TLS. For example, when we say we need SSL (force secure connection) for a website, we actually mean HTTPS is required and will be implemented using TLS.
TLS Handshake
When a client such browser want to connect a server over HTTPS, they begin with TLS handshake. TLS handshake is a series of messages, exchanged by a client and a server to setup a an agreement on encryption strategy for further conversation.
Client will ask (Client Hello) the web server to identify itself and communicates supported cipher suites and TLS version etc.. Server will respond (Server Hello) and agrees on TLS version and cipher suites. It also sends a copy of its SSL certificate (public key), indicating website you are visiting is trustworthy. Client makes sure it can trust the certificate authority (already have the list of trusted authorities) and performs a key exchange with the server. This response is encrypted using server’s public key and web server responds back indicating SSL session is established.
Thus TLS handshake allows both the parties to verify each other, negotiate cipher suites, TLS versions and other attributes required to establish a secure connection. Now further communication between the computer and web server is encrypted!
CA – Certificate Authorities
These are the entities that issue digital certificates (SSL certificates). These certificate is installed into our website and served to browser each time we browse to the website over HTTPS. Certificate Authorities act as a trusted third party by both the client browser and website owner.
Let’s take an example of Secumantra, we already know it is served over https. Remember the pad lock and https in the website URL! Let’s click and look at who issues the certificate. You can see CloudFlare has issued this certificate. As a homework, you can check CA for any HTTPS website already open in your browser now.
There are many such CA all over the world and each browser has the list of CAs it trusts. Few examples are Symantec, GeoTrust, Comodo, DigiCert, Google etc.. Being a CA is a big responsibility and CAs are an essential part of HTTPS communication.
You have to purchase a certificate which involves cost. Now this cost has come down over the years, but one has to purchase/renew it annually. It might be a complex and time consuming for small business and personal sites.
Today this is not a real problem and it can easily be done using sites like Let’s Encrypt or CloudFlare. That too absolutely free! You can follow the article and make your website secure using Cloudflare. For development purposes, if you want to test HTTPS you can create a self signed certificate as well.
HTTPS Today!
As HTTPS plays a very important role in modern web, usage of HTTS has increased dramatically. Many website are opting HTTPS whether sensitive data is exchanged or not. Here is an example showing big rise in HTTPS in just last five years.
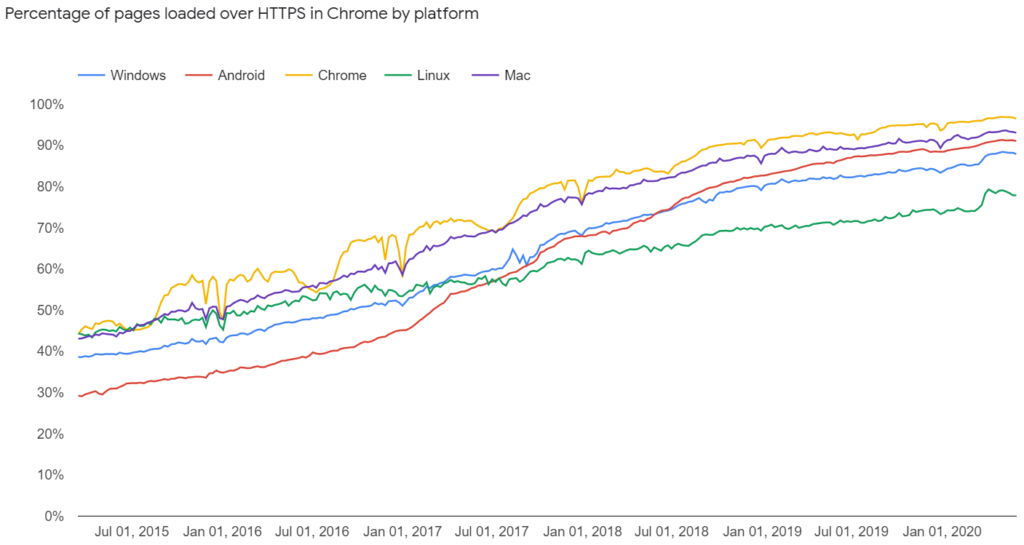
HTTPS is not just limited to banking or personal data sharing sites or social networing sites. We find it on many blogging sites, news sites where we are just reading something. It is no more just about privacy, but there are multiple benefits. Here is a short list –
- Most of the browsers are now giving visual feedback to the user whether website is serving securely or not. You definitely don’t want the browser to flag your site as “Not Secure”.
- Secured website feels more trustworthy and there is a feeling of being safe when a user wants to visit your website.
- Google will penalize your website in search rankings if it is not served over HTTPS.
Conclusion
When we use HTTPS, all requests are transmitted using a secured channel and data is encrypted during transit. It basically helps us to achieve confidentiality, integrity and authenticity.
It is very important to have HTTPS everywhere. Non encrypted traffic can be abused in many different ways. So you should also plan to migrate your site to use HTTPS if not done it already.
It was a quite long post, hope you enjoyed reading. Stay Safe, Stay Secure!