Understanding the CIA Triad: The Foundation of Information Security
In the ever-evolving landscape of cybersecurity, it’s crucial to have a solid foundation to build upon. One such foundational concept is the CIA Triad, which stands for Confidentiality, Integrity, and Availability. This framework serves as a cornerstone for designing, implementing, and managing information security within organizations. In this blog post, we’ll delve into the CIA Triad, exploring each component and its significance in protecting sensitive information.
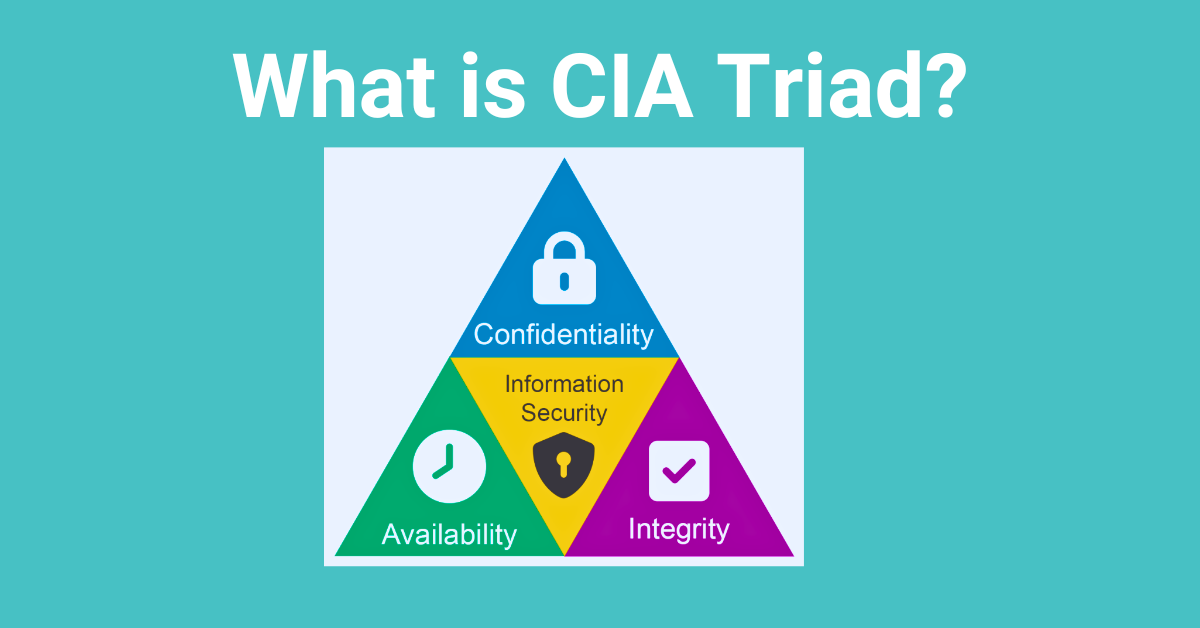
What is the CIA Triad?
The CIA Triad is a widely recognized model used to guide policies for information security within an organization. It encompasses three core principles:
- Confidentiality: This principle ensures that sensitive information is only accessible to authorized individuals or systems. Confidentiality measures aim to prevent unauthorized access, disclosure, or exposure of sensitive data. Examples of confidential information include personal data, financial records, intellectual property, and trade secrets.
- Integrity: Integrity refers to the trustworthiness and accuracy of data throughout its lifecycle. It involves protecting data from unauthorized modification, deletion, or tampering. Maintaining data integrity is essential for ensuring the reliability and consistency of information. Data integrity measures include check-sums, digital signatures, access controls, and data validation mechanisms.
- Availability: Availability ensures that data and resources are accessible and usable when needed by authorized users. It involves preventing disruptions, downtime, or denial of service attacks that could impact the availability of critical systems and services. Availability measures include redundancy, fault tolerance, disaster recovery planning, and robust network infrastructure.
Importance of the CIA Triad
The CIA Triad provides a holistic framework for addressing various security concerns and mitigating risks effectively. Here’s why each component is essential:
- Confidentiality: Protecting sensitive information from unauthorized access helps maintain privacy, compliance with regulations (such as GDPR, HIPAA), and safeguarding intellectual property. Breaches in confidentiality can lead to data leaks, identity theft, financial losses, and reputational damage.
- Integrity: Ensuring the accuracy and trustworthiness of data is crucial for making informed decisions, maintaining trust with stakeholders, and preserving the reliability of business operations. Without data integrity, organizations risk making decisions based on inaccurate or manipulated information, leading to financial losses, legal liabilities, and operational disruptions.
- Availability: Reliable access to data and resources is vital for supporting business continuity, productivity, and customer satisfaction. Downtime or disruptions can result in lost revenue, decreased productivity, damage to reputation, and customer dissatisfaction. By ensuring availability, organizations can minimize the impact of service disruptions and maintain operational resilience.
Implementing the CIA Triad
To effectively implement the CIA Triad, organizations should adopt a comprehensive approach to information security, including:
- Risk Assessment: Identify and assess potential threats, vulnerabilities, and risks to confidentiality, integrity, and availability. Conduct regular risk assessments to prioritize security measures and allocate resources effectively.
- Access Controls: Implement strong authentication mechanisms, authorization policies, and encryption protocols to control access to sensitive data and resources. Employ least privilege principles to limit access rights based on job roles and responsibilities.
- Data Protection: Utilize encryption, access controls, data masking, and secure transmission protocols to protect data at rest, in transit, and in use. Implement data loss prevention (DLP) solutions to prevent unauthorized data disclosure.
- Monitoring and Detection: Deploy intrusion detection systems (IDS), intrusion prevention systems (IPS), security information and event management (SIEM) solutions, and network monitoring tools to detect and respond to security incidents promptly.
- Incident Response: Develop and implement incident response plans, procedures, and protocols to address security incidents, breaches, and disruptions effectively. Conduct regular incident response drills and exercises to test the effectiveness of response measures.
Conclusion
The CIA Triad provides a fundamental framework for managing information security risks and protecting sensitive data and resources. By prioritizing confidentiality, integrity, and availability, organizations can establish a robust security posture and mitigate the evolving threats posed by cyberattacks, data breaches, and malicious actors. Incorporating the principles of the CIA Triad into security policies, procedures, and practices is essential for safeguarding organizational assets, maintaining regulatory compliance, and preserving stakeholder trust in today’s digital age.
Thank you for reading. Stay Safe, Stay Secure!