OWASP Top Ten – Risk Rating
Welcome to Secumantra! We already learnt what is OWASP and OWASP Top Ten in our previous post. Just to summarize, OWASP Foundation is one of the most respected authorities in the field of web application security and it releases OWASP Top Ten List periodically sharing most common security vulnerabilities.
In this post, we will understand how OWASP defines vulnerabilities and estimate risks around a particular vulnerability. The original idea behind OWASP Top 10 is spreading awareness and not creating some type of standard. The OWASP Top 10 is a technology agnostic guide for managing common web application security risks. It is very frequently referred by security professionals and web application developers.
Application Security Risk
For each of the OWASP Top 10 risks, OWASP refers a common matrix. This matrix will begin looking at the threat agents telling who might the attackers be for this particular risk.
Attack vectors tell us how might the attacker can actually exploit a risk and how will they get into application. Next comes the specific security weaknesses that attack can expose and there might be multiple weaknesses for one risk.
Next thing in this matrix is the controls, we might try and apply multiple controls to each risk. Technical impact depends on the asset being protected and business impact depends on the data this particular application is handling. Please refer below image which explains it in a better way.
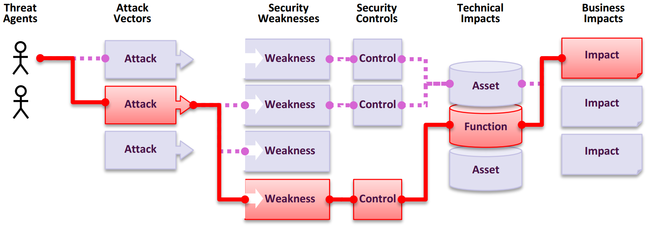
Attackers can potentially use many different paths through your application to do harm to your business or organization. Each of these paths represents a risk that may, or may not, be serious enough to warrant attention.
Sometimes these paths are trivial to find and exploit, and sometimes they are extremely difficult. Similarly, the harm that is caused may be of no consequence, or it may put you out of business.
To determine the risk to your organization, you can evaluate the likelihood associated with each threat agent, attack vector, and security weakness and combine it with an estimate of the technical and business impact to your organization. Together, these factors determine your overall risk.
OWASP Risk Rating
Most of the security incidents result from the flaws in the software design, architecture or improper coding practices. Threat modeling can be useful to identify security concerns in the architecture or design at early stage of software life cycle. At later stage, code review or security scanning can be useful and sometimes security issues may not even be discovered until it is actually compromised.
It is not just about discovering a vulnerability, but one shall be able to estimate the associated risk to the business as well. Ideally, there should be a universal risk rating system that would accurately estimate all risks for all organizations. But a vulnerability that is critical to one organization may not be very important to another.
OWASP has proposed a systematic risk rating methodology and it is possible to estimate the severity of all of risks to the business and make an informed decision about what to do about those risks. The OWASP approach is based on the standard risk model:
Risk = Likelihood * Impact
The risk rating methodology includes six sequences of actions around likelihood and impact.
- Step 1: Identifying a Risk
- Step 2: Factors for Estimating Likelihood
- Step 3: Factors for Estimating Impact
- Step 4: Determining Severity of the Risk
- Step 5: Deciding What to Fix
- Step 6: Customizing Your Risk Rating Model
It helps organizations to prioritize, ensure they don’t ignore the serious risks and at the same time, they are not distracted by the minor risks. Many large organizations might have similar risk analysis framework customized to suit their security requirements depending on the business, data being handled and other factors.
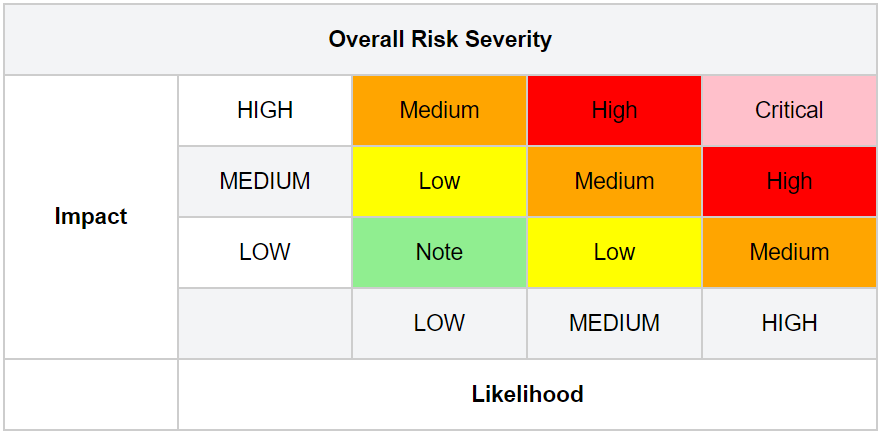
We will revisit this matrix when we talk about each risk separately and will assess each one against a basic traffic light system. It helps us to give a visual idea of relative risk against the other risks in the Top 10 and it is a kind of grading system provided by OWASP. For more details, please visit OWASP Risk Rating Methodology page.
Here is the summary of OWASP Top Ten 2017 Application Security Risks and the risk factors assigned to each risk. Note that these factors are determined based on the available statistics and the experience of the OWASP Top 10 team. We must consider our own specific threat agents and business impacts to come up with the risk for a particular application or organization

It might happen that a severe software weaknesses may not be a serious risk if there are no threat agents in a position to perform the necessary attack or the business impact is negligible for the assets involved.
Defense In Depth
When we try to protect against a risk, there should not just be single defense that put in place. We shall always try to keep multiple barriers and lay out these defenses at different places so that there is no single point of failure.
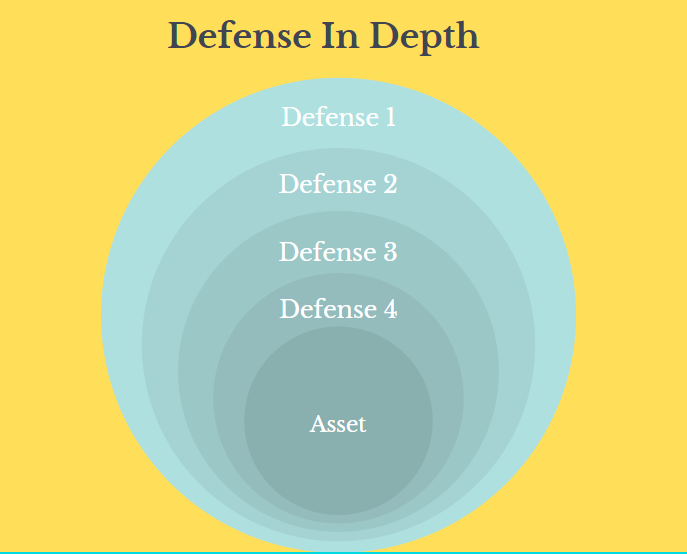
For example, consider cryptographic storage of passwords. So it is only when an attacker gains access to the passwords in storage, real data is compromised. But up stream there we shall have multiple defenses to try and keep an attacker out of our storage to begin with. So in this case cryptography is a last line of defense, a deep defense. It’s several layers under the other defenses and this is an extremely important aspect we need to understand.
Summary
We need to understand that security doesn’t end at OWASP Top 10, rather it is just a starting point. It is an excellent resource for software developers and security professionals to begin with. OWASP also provides a systematic methodology to determine the risk using likelihood and impact of a particular security threat. We also learnt that defense in depth is a very important strategy against any security threat.
Thank you for reading. Stay Safe, Stay Secure!







